From API-last to API-first: A Digital Transformation Story
Nov 13, 2024
ecommerce

When a mid-sized sports equipment retailer with both physical and online presence decided to modernize their operations by migrating to a cloud-based ERP system, they didn't expect to uncover a critical security vulnerability that was costing them thousands of dollars in unnecessary compute resources. This is their journey from being an API-last to an API-first company, and how TypeAuth helped them secure their digital transformation.
The Challenge: Growing Pains in Digital Transformation
The transformation began when the retail company's technical team realized they were losing money without even knowing it. Their migration to a new ERP system had exposed them to risks they hadn't considered before.
The journey began when they decided to consolidate their operations under a single cloud-based ERP system. Their legacy setup, which involved multiple disconnected systems, was becoming increasingly difficult to maintain and was holding back their growth plans.
The Unexpected Crisis
Within weeks of launching their new ERP integration, the company started experiencing unusual patterns in their system performance. Their API endpoints were being hammered with requests, causing their cloud costs to skyrocket and their ERP system to slow down dramatically during peak hours.
The technical team discovered that bad actors had identified their API endpoints and were directly accessing their product inventory and pricing systems. Competitors were scraping their entire catalog every few minutes, while others were running automated price comparison tools against their API.
The numbers were alarming:
60% of API calls were from unauthorized sources
Cloud costs increased by 300% in the first month
Average API response time degraded from 200ms to 2s
Customer satisfaction dropped by 15%
The TypeAuth Solution
After evaluating several solutions, the team implemented TypeAuth to secure their API infrastructure. The implementation process followed three key phases:
1. Authentication Profile with Token Rate Limit
2. Application profile
The Results
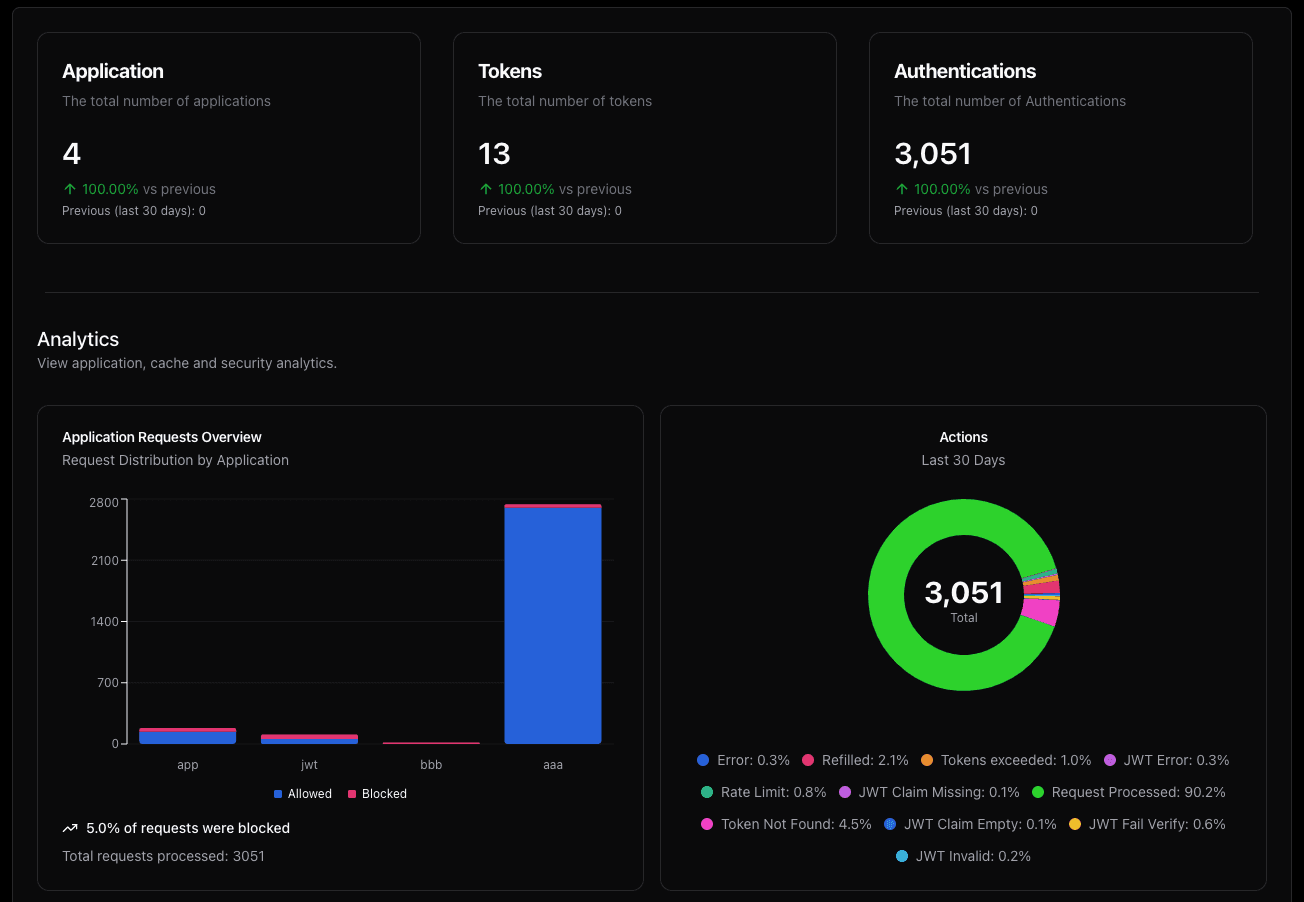
Within just one month of implementing TypeAuth, the team saw dramatic improvements:
Unauthorized API access dropped to nearly zero
Cloud costs decreased by 70%
API response times returned to normal levels
Customer satisfaction improved by 20%
The implementation of TypeAuth didn't just solve their security problems; it transformed how the organization thinks about API infrastructure. They're now building new features with an API-first mindset, knowing they have the security infrastructure to support it.
Key Learnings
Start with Security: Don't wait for a crisis to implement API security measures
Monitor Everything: Implement comprehensive monitoring to catch unusual patterns early
Choose Flexible Solutions: Select tools that can grow with your business needs
Education is Key: Train your development team on API security best practices
Looking Forward
The retail company is now expanding their e-commerce operations with confidence. They're launching a mobile app and partner integration program, all built on their secure API infrastructure.
Getting Started
If your organization is considering a similar transformation, here are the key steps to get started with TypeAuth:
Audit your current API usage and security measures
Identify potential vulnerabilities and access patterns
Implement TypeAuth with a phased approach
Monitor and adjust based on real usage data
For more information about implementing TypeAuth in your organization, visit our documentation or contact our team for a consultation.
Remember: In today's digital landscape, being API-first isn't just about technology—it's about building a secure foundation for your business's future growth.