JWT vs API Key Auth for Machine to Machine APIs: Making the Right Choice
Sep 20, 2024
Authentication
When building APIs for machine-to-machine (M2M) communication, choosing the right authentication method is crucial for security, scalability, and developer experience. Two of the most popular options are JSON Web Tokens (JWTs) and API Keys. Let's explore when to use each one and their key differences.
Understanding the Basics
API Keys
API keys are simple, single string tokens that act as unique identifiers for applications or services. Think of them as a long password that identifies and authenticates the client making the request. They're typically random strings that are hard to guess and easy to revoke.
JSON Web Tokens (JWTs)
JWTs are encoded strings divided into three parts: header, payload, and signature. They can carry additional information (claims) about the client and are signed to ensure integrity. Unlike API keys, JWTs can be configured to expire automatically and contain metadata about the token itself.
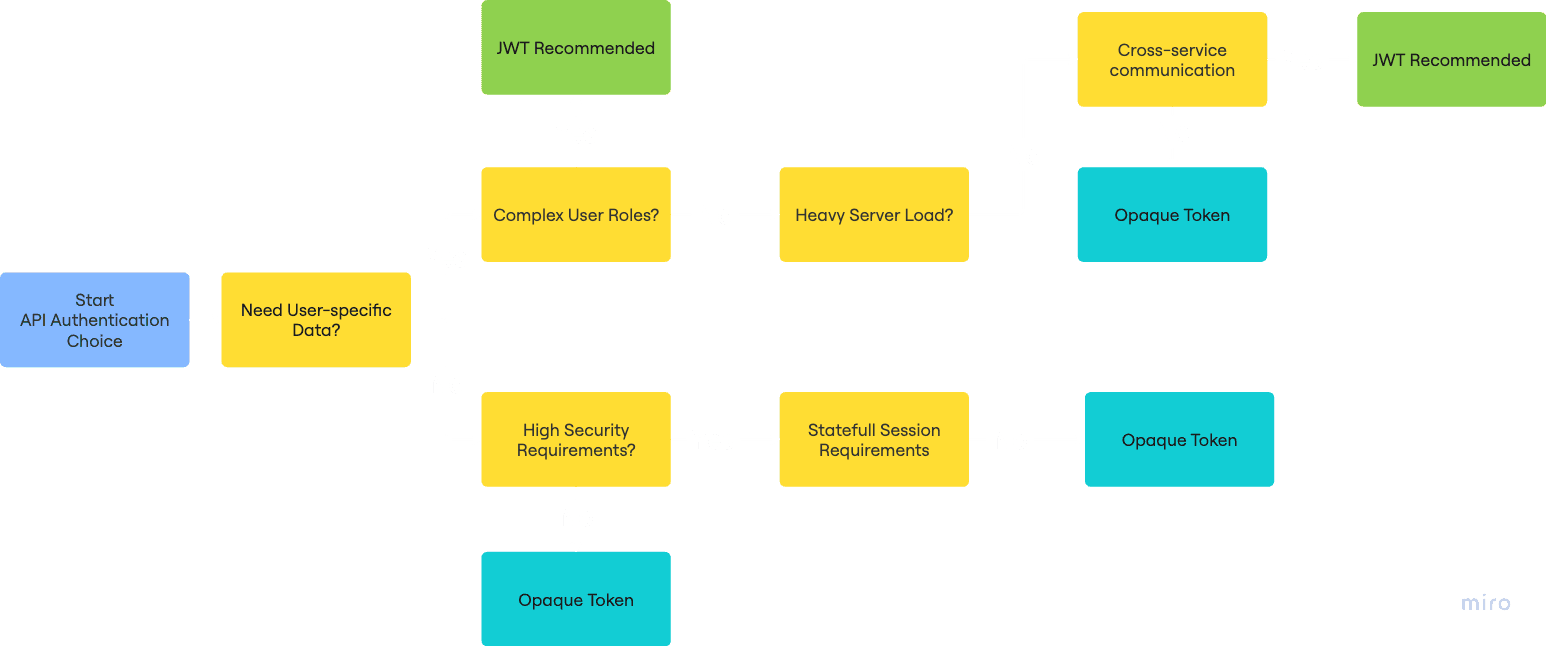
When to Choose API Keys
API keys shine in several scenarios:
1. Simple Integration Needs
- Perfect for straightforward integrations where you just need to identify the client
- Ideal for public APIs with basic rate limiting requirements
- Great for developers who want to start integrating quickly
2. Long-lived Access
- When tokens don't need to expire
- For persistent service-to-service communication
- In scenarios where token rotation isn't a primary concern
3. Rate Limiting Focus
- When your main concern is tracking and limiting API usage
- For implementing tiered API access
- When you need to monitor usage patterns per client
When to Choose JWTs
JWTs are preferred in these cases:
1. Rich Client Information
- When you need to transmit verified client metadata
- For carrying authorization scopes and permissions
- When client identity includes multiple attributes
Security Requirements
- When token expiration is mandatory
- If you need cryptographic signature verification
- When tokens must be validated without a database lookup
3. Distributed Systems
- In microservices architectures
- When tokens need to be verified across multiple services
- For maintaining stateless authentication
Implementation Considerations
API Keys
- Storage: Require secure database storage
- Validation: Simple lookup and comparison
- Management: Easy to generate and revoke
- Overhead: Minimal processing required
- Rate Limiting: Straightforward implementation
JWTs
- Storage: No server storage needed for validation
- Validation: Requires cryptographic verification
- Management: More complex with key rotation
- Overhead: Additional processing for signing/verification
- Rate Limiting: Requires additional infrastructure
Best Practices for Both
Regardless of your choice, consider these security practices:
1. Transport Security
- Always use HTTPS
- Implement request signing when needed
- Use secure headers
2. Token Management
- Implement secure distribution methods
- Plan for token revocation
- Monitor for suspicious usage patterns
3. Access Control
- Define clear scope limitations
- Implement proper rate limiting
- Log all authentication attempts
Making the Decision
Choose API Keys when:
- You need simple authentication
- Database lookups aren't a performance concern
- Token expiration isn't required
- You want straightforward implementation
Choose JWTs when:
- You need to transmit verified information
- Token validation must be stateless
- Automatic expiration is required
- You have distributed system requirements
The Role of Rate Limiting
Both authentication methods benefit from proper rate limiting implementation:
1. Request Patterns
- Monitor usage patterns
- Implement graduated rate limits
- Set up alerts for unusual activity
2. Resource Protection
- Prevent API abuse
- Protect backend services
- Ensure fair usage
3. Business Rules
- Implement tiered access levels
- Track usage for billing
- Manage service quotas
Conclusion
The choice between JWTs and API Keys often comes down to your specific needs. API Keys offer simplicity and ease of implementation, while JWTs provide more flexibility and features at the cost of additional complexity. Consider your security requirements, system architecture, and developer experience when making your decision.
Remember that both methods can be equally secure when implemented correctly and combined with proper rate limiting, monitoring, and security practices. The key is choosing the right tool for your specific use case and implementing it according to best practices.

